Writing a blog post may seem like a simple task, but when it comes to technical topics like task logins, it requires detailed attention and structure. Task logins play an essential role in securing user access to systems, and a comprehensive blog post can help your readers understand every part of the process.
What is a Task Login?
A task login refers to the step-by-step process required for a user to log into a system, such as an app or website. Task logins typically include multiple security measures such as account registration, email verification, and multi-factor authentication (MFA). These steps ensure that users are granted access securely, and they also allow the website or app to maintain a secure environment.
The Role of Task-Based Logins in Websites
Task-based logins not only improve security but also contribute to a better user experience. They protect sensitive user data and allow users to access personalized content, while reducing the risks of unauthorized access.
For example, a user logging into an online banking platform might need to verify their identity with a security question or an OTP (one-time password). Such multi-step logins provide security while still allowing ease of access.
Also Read : Novopay Retailer Login: A Comprehensive Step-by-Step Guide
Steps to Create a Task Login:
Task 1: Registering an Account
The first step of the login process begins with account registration. Most websites require users to create an account by entering details like their name, email, and a password. Some platforms also require additional details such as phone numbers or security questions.
Task 2: Email Verification
After account registration, the user usually receives an email verification link. This step ensures that the provided email is valid and helps prevent spam or fake accounts from being created.
Task 3: Logging into the System
Once the account is verified, the user can log in by entering their credentials (email and password) on the login page. For high-security systems, additional layers of verification, such as MFA, may be required.
How to Write a Comprehensive Blog Post on Task Logins
When writing a blog post on task logins, the main goal is to make the process easy to understand for the reader, even if they are not technical experts.
Understanding the Audience
First and foremost, you must understand the target audience. Are you writing for developers who already know how to build login systems, or are you targeting regular users who just want to understand how to log in securely?
Outlining the Process
Once you know your audience, outline the steps of the login process in a logical order. Readers appreciate clear, step-by-step instructions, and this will make it easier for them to follow along.
Including Technical Details
If your audience is more technically inclined, feel free to include code snippets or mention specific tools that developers can use to build task logins. If not, keep the technical jargon to a minimum and focus on the user experience.
Step-by-Step Guide to Writing a Task Login Blog Post
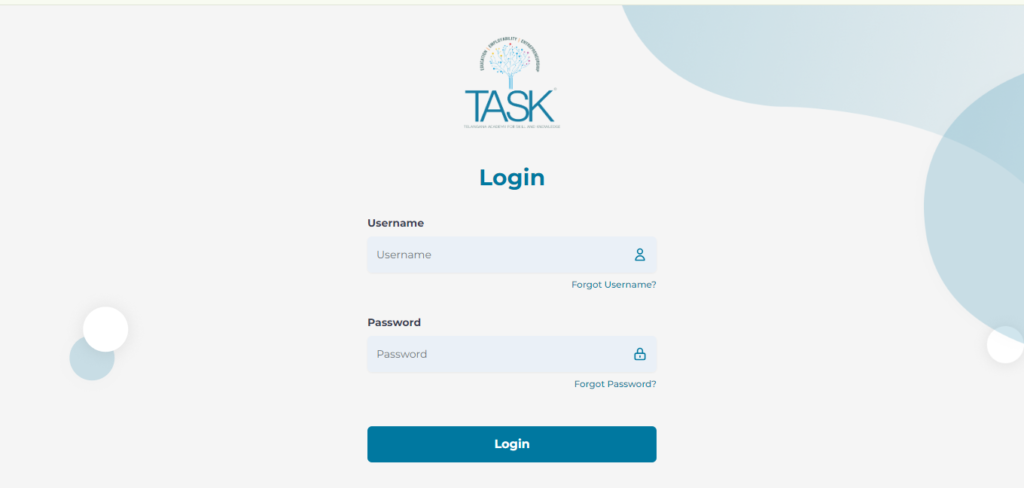
Step 1: Introduce the Concept of Task Logins
Start your blog post by introducing the importance of task logins. Explain what they are and why they matter in today’s security-conscious world. Provide examples of where task-based logins are commonly used.
Step 2: Break Down the Login Process
Break down the entire process of task logins into smaller steps. Make sure to include:
- Registration
- Verification
- Multi-factor authentication (if applicable)
Step 3: Provide Screenshots and Examples
Use visual aids, such as screenshots, to show each step of the process. For example, display how an email verification screen looks or show a step-by-step illustration of setting up MFA. This helps make the process more engaging and easier to understand.
The Importance of Detailing Each Step
Detailing every step ensures that the user does not miss out on any critical information. It also helps to reduce confusion, especially if the login process involves multiple layers of authentication.
Examples of Task-Based Logins in Different Industries
- E-commerce: Users logging into their account to complete purchases.
- Banking: High-security logins involving MFA for online banking.
- Social Media: Standard email and password logins with optional 2FA (two-factor authentication).
Structuring the Blog for Better Readability
To make your blog post more readable, use a logical structure:
- Headings and subheadings to break up content.
- Use bullet points and numbered lists to make the steps easy to follow.
Common Mistakes to Avoid in Task Login Blogs
Some common mistakes to avoid include:
- Skipping important steps in the process.
- Overcomplicating the explanation with too much technical jargon.
Why Task Logins Matter for Security
The importance of task-based logins cannot be overstated, especially in today’s digital age, where cybersecurity threats are constantly evolving. Task logins are integral to protecting personal information, financial details, and sensitive data from being accessed by unauthorized users.
Think of your online banking login process—it doesn’t just stop at entering your password. Many systems now use multi-factor authentication (MFA), which might include receiving a code on your phone or answering a security question. These extra steps act as safety nets, ensuring that only the right person gets through. This is why task logins are essential in reducing the risks of hacking and data breaches.
Multi-Factor Authentication (MFA): A Critical Component
Multi-factor authentication (MFA) is increasingly becoming a standard practice for task logins. It requires users to provide two or more pieces of evidence (factors) before they can access their account. This might involve:
- Something you know: Like a password or PIN.
- Something you have: Like a phone or a security token.
- Something you are: Like biometric data (fingerprints, facial recognition).
When creating your blog post, it’s important to stress how MFA improves login security. You could also include tips for users on how to enable MFA in their accounts or recommend trusted MFA applications like Google Authenticator or Authy.
Breaking Down the Technical Details
For developers or technical audiences, including the nitty-gritty details of how a task login is constructed on the backend can be immensely valuable. You can mention different programming languages and libraries used to create secure login systems, such as:
- JavaScript frameworks (e.g., Node.js for backend security).
- Python for secure authentication flows.
- OAuth and OpenID for secure login protocols.
Explain how these tools are implemented to create a seamless login experience, making your blog not only helpful for users but also educational for developers.
Common Issues Users Face with Task Logins
Users often encounter problems when logging in, especially when security measures become too complex or confusing. Highlighting these challenges in your blog can help readers understand what to look out for, as well as how to avoid frustrating errors. Common issues include:
- Forgotten passwords: Encourage users to use password managers to store their credentials safely.
- Failed MFA authentication: Explain that users should ensure their devices are synced and that the authentication codes match.
- Locked accounts: Outline how users can regain access, either through password resets or contacting customer support.
Best Practices for Writing User-Friendly Login Tutorials
When writing a blog post on task logins, clarity is key. Technical topics can be overwhelming if not presented in an organized, easy-to-follow manner. Here are some best practices for creating tutorials that your readers will love:
- Use Simple Language: Avoid using too much jargon, and where technical terms are necessary, provide brief explanations.
- Short Paragraphs: Break content down into digestible chunks. Long paragraphs can be tiring to read, especially for users scanning through for specific answers.
- Visual Aids: Images, diagrams, and screenshots go a long way in helping users understand complex steps. An image showing how to enable two-factor authentication can often be more effective than a paragraph of text.
- Numbered Steps: Guide your readers through the process using numbered steps. For example:
- Step 1: Go to the login page.
- Step 2: Enter your credentials.
- Step 3: Complete MFA if prompted.
This approach helps readers keep track of where they are in the process.
The Future of Task-Based Logins
As technology evolves, the future of task-based logins will likely involve more biometric data and AI-driven authentication methods. Facial recognition, voice verification, and fingerprint scanners are already becoming commonplace, especially on mobile devices. Discussing these emerging trends in your blog can make it more forward-looking and insightful.
Conclusion
Task logins are fundamental to secure, user-friendly access to digital systems. Writing a comprehensive blog post on the subject involves not only outlining each step of the login process but also providing context on why these steps are important. By breaking down the technical details and offering clear, actionable instructions, you can create an engaging and informative post that will be valuable for your readers.
Also Read : Micronavdisha Login: A Comprehensive Step-by-Step Guide | Novopay Retailer Login: A Comprehensive Step-by-Step Guide
FAQs
1.What are task logins?
Task logins refer to the process by which users register, verify, and authenticate themselves before gaining access to a system. This can include multi-factor authentication for added security.
2.How does multi-factor authentication (MFA) enhance login security?
MFA requires users to provide two or more verification factors, such as a password and a code sent to their phone, making it harder for unauthorized individuals to gain access.
3.What common issues do users face with task logins?
Common issues include forgotten passwords, failed MFA, and locked accounts. These problems can often be solved by using password managers or contacting customer support for assistance.
4.What tools can I use to enhance my task login blog post?
Tools like Trello or Jira can help in tracking login steps, while screenshot tools like Snagit can provide helpful visuals to accompany the text.
5.What’s the future of task logins?
The future of task logins is likely to involve more biometric-based methods like facial recognition and AI-driven authentication, making logins faster and more secure.



